analysis A treasure trove of previously confidential documents pertaining to the Government’s data retention policy and released this week under Freedom of Information laws display an astonishing technical ineptitude on the part of the Attorney-General’s Department with respect to the controversial project.
For most Australian residents even casually concerned about the encroachment of government surveillance into their privacy rights, the term ‘data retention’ has the potential to deliver a note of terror, or at least mild anxiety. Conceived behind closed doors by the Federal Attorney-General’s Department in the years from around 2008, first revealed publicly in mid-2010 and now the subject of a fraught parliamentary committee process, data retention is the Big Bad of government surveillance. All your phone calls, all your emails, and potentially even all your web site visits and social networking interactions; tracked, archived, and made available for casual browsing by law enforcement authorities; sometimes without even a warrant.
But if you believe some of the revelations contained in an astonishing series of confidential documents extracted by the Pirate Party from the clutches of the Attorney-General’s Department this week … many of the key players pushing the policy in the Federal Government may not have a very solid grasp on the technology behind it.
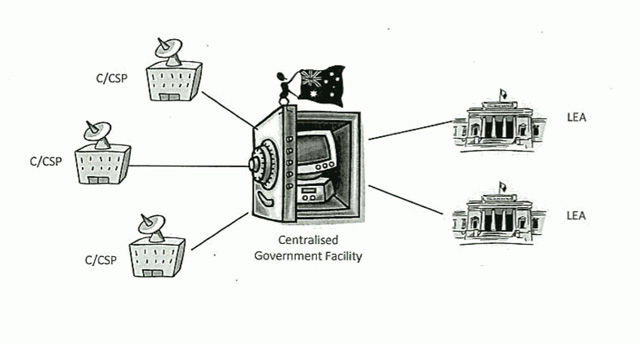
Take this network operating model which the Attorney-General’s Department put together in 2009 to distribute to Australian ISPs as one example of how a data retention system could work in practice:
The first thing the observer may notice is that there’s something incredibly macabre about the fact that the Attorney-General’s Department went to the effort of producing such a cute diagram to represent such a disturbing program, complete with an ant-like figure waving an Australian flag sitting on a cute PC locked in a safe to illustrate its planned “Centralised Government Facility” for data retention. (a name that would not have been out of place in Stalin’s Soviet Russia). What kind of person dresses up an Orwellian government surveillance program with cute icons?
But the more important fact is how frighteningly naive such a depiction is.
iiNet, only the third-largest ISP in Australia, has publicly estimated that the cost to its own business of delivering the data retention scheme conceived by the Attorney-General’s Department, which would store up to two years’ worth of Australians’ data, would soak up some 20,000 terabytes and cost some $60 million to administer.
The mind boggles when you start to consider how much more data Optus and Telstra, both substantially larger than iiNet, would need to store in such a facility, and how much it would cost. Telstra certainly seems to think it would be prohibitively expensive. The sheer process of storing and organising that much data would doubtless soak up hundreds of jobs and hundreds of millions of dollars. And that’s if it even worked at all. Australia’s Governments have repeatedly shown they have poor governance skills when it comes to implementing massive IT projects (Queensland Health, anyone?) and securing their own infrastructure (see examples here, here and here). When literally all of Australia’s communications is in the picture, how much more frightening that picture must be. And let’s not forget that other great storehouse of sensitive Australian information, the Personally Controlled Electronic Health Record project, was hacked before it even launched.
Hardly the cute and breezy picture the Attorney-General’s Department paints in its diagram.
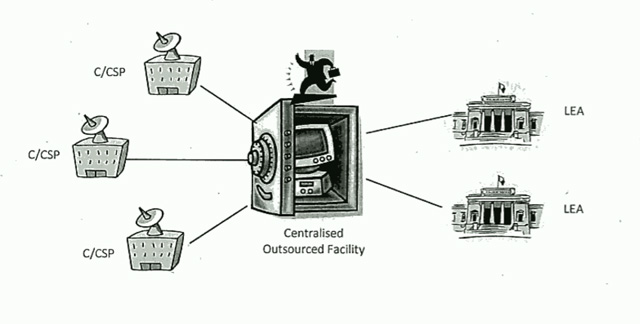
Similarly naive is the next model the department proposed; where an outsourcer would control the data storage. Again, here the same technical limitations arise; but there are also others; controlling the outsourcer itself. Again, here Australian Governments have shown themselves to have a poor track record when it comes to governance of such an outsourcing relationship.
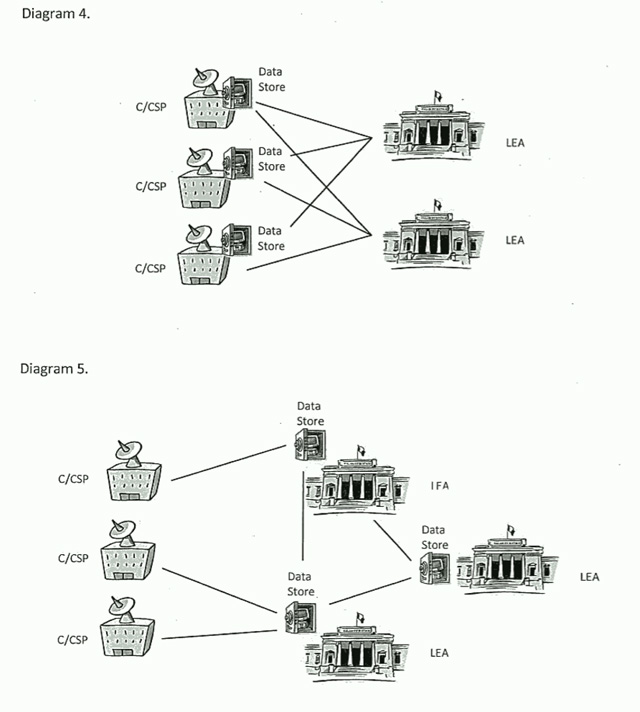
And then things get worse. We start to get into composite situations; ISPs, outsourcers and law enforcement entities all storing data; with these collossal datasets being “interlinked” and with data being swapped all over the place. Charming. Again, data transferral on this scale is far from a trivial task. The glibness of these diagrams starkly illustrates that the Attorney-General’s Department simply has no idea what it is talking about when it comes to the technical complexities of managing huge datasets.
“Do you favor any of the previously described models?” the Attorney-General’s Department glibly asks ISPs at the conclusion of its consultation paper. “If not, additional suggestions are welcomed.” The mind boggles. This is total government surveillance — conducted cowboy-style.
Later on, other documents reveal that in 2009, the Attorney-General’s Department had not determined “who will pay” for the whole deal — but that existing cost-sharing arrangements in telecommunications interception could apply. Again, this displays an incredible naivity surrounding the Attorney-General’s Department’s understanding of the costs involved. Under current TI legislation, Australian ISPs simply do not spend tens to hundreds of millions of dollars satisfying these kinds of government requests.
We’re talking here about a cost and IT infrastructure change from an existing telecommunications scheme in which Australian telcos and ISPs respond collectively to interception requests in the order of several hundred thousand per year, to a system in which every one of the billions of telephone and Internet interactions Australians conduct every year are logged. Its documents reveal the Attorney-General’s Department doesn’t quite seem to realise the exponential scale of telecommunications interception it’s planning with its data retention regime.
By 2011, the Attorney-General’s Department was beginning to realise the difficulty of some of these issues, as ISPs made their views clear (all still behind closed doors, of course). Meeting notes from an “industry forum” held by the Department on the issue note that “costs is a big factor” (sic), but by then other issues had started to raise their heads.
The same document notes that the privacy issues associated with the (hideously cute) “Centralised Government Facility” mentioned earlier would be “insurmountable”. Wow. It doesn’t take a rocket scientist to work out that if you collate all of Australia’s telecommunications data in one place, it will eventually be hacked — especially if the facility was maintained by the Government itself. And that’s not even counting illicit access by staffers who already have approved access to the data. Want to find out if your wife is cheating on you? Have a mate at the “Centralised Government Facility”? No problem. Have him pull a copy of her telephone, email and social networking records. That ought to do it. God knows this kind of thing goes on in the normal Police force on a regular basis.
But again, the next sentence in that document reveals the same deep technical naivity, claiming that such issues could be overcome “with additional security”, and a “spoke and hub arrangement”. Yeah, right. Is there any level of security which could be sufficient, for this kind of project?
Another factor mentioned was that communications technology itself was rapidly changing. Forget Skype, which had been around for years by then; one of the more pressing issues mentioned in the documents was Apple’s revelation in October 2011 of iMessage; a simple instant message protocol that would start replacing the easily trackable SMS format on many iPhones. It doesn’t appear as though the Attorney-General’s Department quite knew what to do about this kind of thing; telcos and ISPs wouldn’t be tracking the IP-based iMessages, after all.
But again, here we must question the incredible naivity of the department. iMessage is nothing new … online, IP-based message protocols had, by 2011, been around for several decades. Perhaps the department could have considered the 1996 launch of the now-defunct ICQ platform, for example, which has never been able to be tracked for telecommunications interception purposes. And there are thousands of other examples of how Internet-based technologies were disrupting carrier telecommunications models.
Written between the lines are other problems. The department’s document mentions that “destruction clauses” for the retained data “would be good” — presumably every year, a year’s worth of data would be deleted.
But, as Google has learnt to its pain over the past several years, the permanent deletion of sensitive data is no easy matter. In a practical sense, how is anyone supposed to go about permanently deleting some 20,000 terabytes of data each year (and remember, that’s just for iiNet)? Magnetic hard disks, the most common storage method, will always retain some of the data they have stored unless completely physically destroyed; and there’s also the fact that the most secure deletion routines (which would surely need to be used in this case) which leave the disk intact consume a great deal of time.
Ever done a low-level format of your hard disk, ‘zeroing’ it out? Now multiply that by a figure in the hundreds of thousands (millions?) each year. Not precisely an easy task.
Then there’s the documents’ curious mention of the fact that “in a converged society, IP address is the most useless identifier, because it will change as you roam”. This is true: IP addresses have long been discredited as a source of hard identification online, as they can be assigned or dropped at will. However, more disturbing is the documents’ mention of a “MAP address” as being more useful. We can take this as an error; most likely the department was referring to the ‘MAC address’ which all IP network devices use as a hardware identifier.
This mention is not concerning because it’s scary that the Government might be able to trace your actions online by your device’s (phone, laptop, tablet, PC, etc) MAC address. It’s concerning because Australian studies have repeatedly emphasised directly to the Attorney-General’s Department that MAC addresses are also a poor method of identification.
Take this 2004 paper by scholars at Swinburne University of Technology’s Centre for Advanced Internet Architectures (PDF), for example. It states baldly:
“In this paper we report on our investigations into the feasibility of using MAC addresses rather than IP addresses as an identifier in Lawful Interception. We found that MAC address interception in PPPoE and Broadband Ethernet environments can be very easily subverted. Consequently, we believe that MAC based interception is a poor option for lawful interception.”
We know that AGD must have been aware of this paper, because Electronic Frontiers Australia directly quoted the paper in its submission to a Senate inquiry into the then-Telecommunications Interception Act in 2006. Furthermore, the Law Council of Australia’s submission into the 2008 Inquiry into an amendment bill (PDF) at the time to the same act (funny how often Australia’s telecommunications interception regime gets amended, isn’t it) also notes it has concerns about the use of MAC addresses as identifiers.
And yet AGD was still discussing MAC addresses as identifiers in 2011. Hell, it probably still is.
So how does this kind of thing happen? How does a group of bureaucrats demonstrate so much technical naivety about this kind of massive technology project to track almost every aspect of Australia’s telecommunications; a project which inherently requires the most adept of technical competence? A project which clearly requires an experienced project governance team, high-level support from chief information officer- and chief security officer-level staff and massive financial resources? The answer is clear: The public servants behind this project do not have the technical experience or competence to implement it.
The two most high-profile AGD public servants behind the project are Catherine Smith, assistant secretary, telecommunications and surveillance law branch, and Wendy Kelly, director of the same branch. To be honest, we know very little about this pair; for all that they are the public face of a project generally considered to be one of the most sinister and ill-considered efforts that any Australian Government has ever come up with. There are no online biographies for these two; no articles laying out their principles; no photos, no LinkedIn profiles; almost nothing, in fact, apart from sporadic appearances before Senate committees which they only reluctantly attend.
But if they are like many of the other senior bureaucrats at AGD, it’s possible to make a decent guess at their background. They’re probably lawyers or have a background in law enforcement and public administration. How do we know this? Just look at everyone else who runs things at AGD.
I don’t know for sure that the department’s secretary, Roger Wilkins (you remember, the bureaucrat who set up the secret anti-piracy meetings between the ISP and content industries) is a lawyer, but he’s certainly been involved in plenty of law reform in his time in government. Deputy Secretary Elizabeth Kelly is a former lawyer and has worked in attorney’s and justice departments for years. Deputy Secretary David Fredericks is a lawyer, and the department’s other Deputy Secretary, Tony Sheehan, has a background in addressing issues such as “terrorism and people smuggling”.
Check out their biographies. Do these look like the kinds of people who, if they were overseeing a technology project of gargantuan proportions, would know what they were doing? Not really. It’s not their fault, but they just don’t seem to have the technical experience required. And they probably don’t understand all of what Kelly, Smith, AFP cybercrime chief Neil Gaughan and the telecommunications industry are talking about when it comes to data retention. Yet it’s these kinds of bureaucrats who are responsible for top-level oversight of the development of projects such as the data retention initiative. These departmental bureaucrats aren’t CIOs; and one has to suspect that even an experienced CIO would have trouble grappling with the technical issues inherent in this data retention disaster.
After I read through the documents which the Pirate Party’s Brendan Molloy had succeeded this week in dragging out of the Attorney-General’s Department, I also read this highly insightful piece by Crikey correspondent Bernard Keane. I recommend you do the same; in my analysis today, I drew mostly on the technical aspects of the documents, whereas Keane is more expert in the legal and regulatory implications.
But overall I think we both got the same feel from this highly confidential material. They paint a highly disturbing picture of a group of obscure bureaucrats working in complete secrecy, yet with the support of the highest levels of government (up to the office of the Prime Minister itself), to cast an incredibly massive net of surveillance over the entirety of Australian society; and doing so in an, at times, incredibly incompetent manner.
These are children attempting to play God with dangerous weapons they do not understand. Let us hope fervently that Parliament knocks back this dastardly proposal and that light continues to be shone in all the cracks in the Attorney-General’s Department. Because I’m sure that if a proposal like this existed for so long unknown, then there will be others still un-heard of.


Nothing scares me more in all my adult life than the idea this legislation will get through. It may be encouragement enough to consider finding a new country to pledge my loyalty.
Scares me too! That’s why we have to fight it; because we care about the future of ‘Straya
wooo clipart!
The system to process all this data into some usable form would also cost in the billions of dollars. Maybe they just planned to give other governments or private business access to process it themselves. Given the harebrained nature of the above maybe their thinking did not even extend that far. Surely the actual “law enforcement agencies” that request this system know enough that when the saw the discussion paper they let out a little giggle and a sigh.
Many years ago I had a sysadmin job where I reported directly to the Marketing Director… (hint: if you’re ever in this situation, RUN!). His life motto seemed to be, “How hard can it be?” Of course, the answer is usually, “Actually, surprisingly difficult sometimes – the fact that you don’t realise the difficulty involved means that I’m doing my job properly.”
It’s the same in this situation. We who keep the engine rooms of IT running – sometimes with stickytape, string, and force of will – make stuff happen that might as well be magic to non-technical folk. The logic seems to be, “If I can install a Windows app on my home PC, it mustn’t be that much harder to deploy a nation-spanning data collection and retention system, with unassailable security and access control, right?”
Initiatives like this need to have input from lawyers and LEA-types, sure. But such projects also need to be heavy with deeply-technical folk who have an appreciation for the technical difficulty of the task proposed. And perhaps more importantly, those technical people need to be able to articulate clearly to the non-technical types the true size, scope, and complexity of the project. Enormous, complex projects *can* be delivered – but only when all of the technicalities are well understood by those who are running the show.
Of course, the question that should also be asked in this case is, “Even if we can deliver this capability technically, is it something that we *should* be doing, given the massive security risks and implications for privacy of Australian citizens?” I, like many (most?) others here, am squarely in the ‘Hell NO!’ camp.
itgrrl – you hit the nail on the head. It is also what scares me about most current IT management having no technical background and mistaking a few ITC units in a MBA sausage factory for practical expertise. And it’s only getting worse with direct degrees in project management springing up every where.
The philosophical/ethical issues are also a monstrous tangle, mix pre-crime detection with standard bureaucratic cock-ups and the two losers will be justice and the public.
How this isn’t front page news in every newspaper is almost as large a scandal.
sounds like he walked straight off the pages of the BOFH into reality. those kind of people scare me. those kind of people in government scare the crap out of me.
When they can’t even keep the Parliaments emails safe from hackers (source: http://www.news.com.au/technology/federal-ministers-emails-suspected-of-being-hacked/story-e6frfrnr-1226029713668) this is one of _the_ dumbest ideas this, or maybe even any, government has had.
Mmmm, disturbing.
From the various submissions to the inquiry and the obtaining of documents like this, I’m slowly shutting my view to the idea of a decent policy based around open and clear data retention that I had.
The AGD seems to be on a crusade no one else is interested in. Except maybe ASIO and the cops.
“The AGD seems to be on a crusade no one else is interested in. Except maybe ASIO and the cops.”
They are directed by the government. This is government policy. It’s not the only one of its type. The filter wasn’t dropped because they thought it was bad policy. It was dropped because they couldn’t get it through. Rest assured if the government is returned in September the filter will come back too. Add to that the assault on free speech in the anti-discrimination proposals and proposed government regulation of the media and there’s a lot to worry about with this government.
Sell your freedom for a pound of fibre sir?
Renai,
Do you know if Brandis has said anything about the Coalition’s position on this?
@CMOT
No they’re not. And if they are, then they’ve been directed by BOTH Liberal AND Labor governments, because they’ve been pushing this since Howard.
And that pretty much puts paid to your idea that you’re worried ONLY about THIS government. I’m worried about ANY government that tries to impinge on freedoms. But you’re kidding yourself if you think it’s only Labor.
The article says …
“Conceived behind closed doors by the Federal Attorney-General’s Department in the years from around 2008 …”
Unless Howard hung on after he’d lost the 2007 election and his seat this is ALP government policy. The other policies I mentioned are ALP government policies too. That’s this ALP government and that’s why I’m worried about it.
Sell your freedom for a pound of fibre sir?
@CMOT
And the IDEA has been thrown around since 2004. It took a new government and change of fortunes for the AGD to push it through. Make no mistake, this is being pushed by the AGD.
And do you SERIOUSLY think this would make it through the Senate???
I’ll have my pound of fibre and I’ll each it if this makes it through the Senate.
“And do you SERIOUSLY think this would make it through the Senate???”
I shouldn’t worry about the totalitarian loonies in the House of Reps because the Senate will stop them? Are you serious? How about I don’t vote for the totalitarian loonies? Seems more effective to me.
It happened under this ALP government. It is being pushed by this ALP government. Paint it how you like, it is this ALP government.
Sell your freedom for a pound of fibre sir?
@CMOT
I’m more worried about what this Coalition will do to the economy if they get in, than whether Labor can even get the legislation written for this.
And I’m entirely unconvinced the Coalition won’t proceed along the same lines. They’ve made VERY little comment about it.
“I’m more worried about what this Coalition will do to the economy if they get in, than whether Labor can even get the legislation written for this.”
Yep, but basic freedom and rights come first. Why is this government launching this attack on our freedom and our rights? This is going further than Howard went after 9/11.
“And I’m entirely unconvinced the Coalition won’t proceed along the same lines. They’ve made VERY little comment about it.”
Hence the question in the last line of my first post in this conversation. The flavour of government is irrelevant to my hatred of these sorts of policies.
“Sell your freedom for a pound of fibre sir?”
Don’t be stupid. You’ll have your filter and/or data retention regardless of network build.
“Why is this government launching this attack on our freedom and our rights?”
Good question. However it’s clear we should not trust either the labor party or coalition when it comes to these things. So far only the Greens can really be trusted on this issue. Also you’ll notice it’s not just Australia that wants these silly surveillance laws.
“This is going further than Howard went after 9/11.”
Right. So what exactly do you think allowed them to go further.
I can troll on this too;
Yes I want my fibre instead of my rights.
Because fibre is a physical thing; it is harder to undo than restriction of my rights. If you have so much faith in your coalition government; then we can stick with labor till we have our fibre; then switch over to a coalition government who can reverse all those laws for us!
win win win! with only ~10 years absolute tops of unreasonable surveilance; which if it is so bad will be a really good warning for the future when someone else thinks its a great idea!!
(For the record; I am totally against the surveilance laws, but I can look at the trees instead of the forest too!)
Let me put it to you this way:
How easy is it to correct the Labor party’s erroneous filtering and privacy policies? Almost trivially easy.
How easy is it to correct the Coalition’s erroneous NBN policy? Incredibly difficult and hideously expensive.
Ok, so from a purely logical point of view it would be sensible to back the Labor party on this. While we are at it, let’s look at it from another angle:
How easy is it to work around the Labor party’s erroneous filtering and privacy policies? Almost trivially easy.
How easy is it to work around the Coalition’s erroneous NBN policy? Incredibly difficult and hideously expensive.
So we can back Labor, whose errors will be simple to workaround and simple to fix. Or we can back the Coalition, whose errors will be incredibly difficult and expensive to fix, and basically impossible to workaround.
Only someone blinded by their partisan outlook would back the Coalition – if we are only comparing technology and comms policy. You would have to take the argument far away from telecommunications before the Coalition looks anything other than horrific.
>”made available for casual browsing by law enforcement authorities; sometimes without even a warrant.”
Not quite.
Access to “telecommunications data” does not ever require a court to issue a warrant. No ifs. No buts. This is just one of the many problems with this proposal. This is an existing problem.
From that perspective, Diagram 4 is the least obnoxious of a set of obnoxious choices.
Great article Renai
Cheers, much appreciated!
Re: MAC address ident.
One of my clients is a hosting service.
I admin the BGP routers of which there are two.
One on line and one warm stand-by.
One of our upstream peers blocks all traffic if the MAC changes and it takes a call to their network guys to get the “new” one unblocked.
So I simply put in a line in each of the border NIC configs that makes each of the NICs have the same address as the corresponding NIC in the other router.
I did the lot as it means we will never have a problem with any of the peers who think that a constant MAC is A Good Thing ™.
Too easy….
Can we please call for a ban on any manager, project manager, politician, bean counter, architect, anybody in power to make decisions anywhere from making technical decisions with no technical knowledge. That would make the technical world a bit easier to work in. And would exclude these idiots from making such stupid decisions. Doing anything on your home PC does not make you an expert and definitely does not make you qualified to do anything or make any decisions in/for an enterprise environment.
My comment on ZDNet:
The banality of evil…
… as another commentator has said.
So after everyone asking the question “won’t someone think about the children?”, we now know it was a faceless AGs SES drone who was quietly plotting the largest assault on privacy in the nations history to fulfil the kiddy care meme. Should have gone down a treat at the performance bonus review. Now won’t someone think about the vpns, proxies, carrier pigeons et al? Of course not.
Oh, and good to see the isps supporting our privacy, as long as their bottom line is aok.
Sometimes you pay more than peanuts and still get the monkeys, and as a former one I always thought fed public servants were slightly more cluey than politicians…
If you’re still alive there Renai, this would have to be the most scary bedtime story I’ve ever read. It basically allows anyone with the means (read dollars) to track and or sell any online person’s whereabouts and personal details.
If you had posted this in China you’d be hanging upside down in a dark dungeon by your toenails.
It also paints a picture of how easy it is for a terrorist to shut this county down a la “die hard 4.0” style.
It’s most frightening for those who have something to hide!
I am still alive :)
Who has the authority to sack public servants? This whole project is being driven from within the AG Dept, the bosses of which remain in place no matter which party provides the minister.
If any minister stops the project it can just be reintroduced to the next minister. The only way to stop this is to remove the public servants who have kept it going for all these years and promote some sensible people to take their places.
Australia is approachig the ranks of a sh1t country very rapidly. Cost of living and an idiotic bureaucracy out of control are the worst things . I would be glad to leave Austrlaia for a nother life overseas.
As for this data retention rubbish, Orwell must be rolling in his grave.
VPN to Sweden here I came
My 2 cents
When nbn will go on there be more data then
They handle NSA builds they facility in USA
And 2billion dollars is the stating figure
When it comes to public policy issues with this degree of technical complexity we’re always going to run into limitations in the tech understanding of policymakers.
The intent of the public servants and bureaucrats is to fill in the knowledge gap, but clearly that’s failing badly.
How about this for a solution? We’re obviously not going to be able to change the staffing of existing bureaucracies – nothing short of cataclysm could do that – so logically we need to take the technical design responsibility away from them.
I think we need to find a way to divide the definition of a project’s goals (which can be left in the hands of politicians and bureaucrats) from the design of solutions (which must be provided by specialists).
Politicians will be happier campaigning on the ‘what’ rather than the ‘how’ – it’s what they already do, after all (the NBN debate being a notable exception).
When it comes to the question of how this kind of change should be brought into effect… any ideas? I’m thinking totalitarian regime change (think harder, Homer…)
This is actually how it is supposed to be operating now.
A policy officer in the government doesn’t “make decisions”. They are directed (by their bosses, who are in turn directed by their minister) to solve a certain problem.
In this instance; perhaps it was a report by ASIO or the AFP saying: “We cannot pull records about crimes that have happened in the past, like we can lists of phone numbers dialed from a Telco” (among other things I am sure).
The policy officer calls consultants and other departments that perhaps have relavant information, asking them to list all the detail they can about ways to solve this problem (the problem being the way it was framed by their boss, and from the minister to their boss).
The framing I mention, is the political spin, for instance a dictatorship might frame the question to the policy officer: “Find out all the ways we can do this in total secrecy and learn as much as possible about what people do on the internet; specifically we want alerts when they google “Overthrow Government” etc.”
But, a more reasonable government (reasonable as in; trying to solve a legitimate problem) might say: “What is the best way to allow Law Enforcement to request an as detailed as possible account of someones history on the internet, comparable to a phone-history”
Anyway; the idea is the Policy Officer is meant to obtain a list of options that best suit the question asked of them, write it up so that the stakeholders (the minister in my example) will be able to understand, whilst trying to avoid dumbing it down so much it loses all the actual content of the proposed solution.
So the people in the department are obviously at fault; but probably not for the reason you would expect. Their problem wasn’t what they wrote down, far from it (from the snippet above I am actually impressed overall with the quality) but rather the problem with the report is in the question the policy officer asked the consultants; and the answer the consultants gave.
It always comes down to it in this debate; and that is: Data volume, and Cost. IE the actual specifics of the policy.
Where the ball dropped on that; is any-ones guess. My guess is on the minister for the framing; and the policy officer (or consultant) for not flagging the giant black hole in the request. (Then again; the PO may have even written all that detail in; and on its way up the chain of command – all their bosses have to read and sign off at each level – they sent it back down saying “This is confusing” until it no longer included that detail.)
I might be wrong about all of the above; my experience in the above is 3rd hand; and state government rather than federal. for what it’s worth.
Is that guy in the second image running away with all our data? I assume that the “Centralised Outsourcing Facility” will be in the US, where all the data will be readily available to the US government. But of course, they’re our friends.
Wait until the politicians step in and say “hold on – we need a few exclusions. If you are a currently sitting member, your telecoms data can’t be collected”. (With no idea of the technical cost of such a change).
And for those who have been arguing about which government wants to do this, the answer is both. The only reason this won’t pass through both houses at the moment is back-bench revolt. Otherwise, we might already have a bill establishing the 1984 nation.
So far this is about the only item Abbott hasn’t said “NO!” to.
Last election only the Greens came out against Conjob’s Filter.
So just how did you get the politician to pose and stay still for that photo up there?
Were there bananas involved? ;)
Comments are closed.